This post contains affiliate links.

If you’ve spent any amount of time on the internet, you’ve probably heard of the “dark web”.
But did you know that the dark web is accessed using something called the Tor browser? Did you also know that Tor is readily downloadable and free to use by anyone?
I know what you might be thinking.
Believe it or not, Tor is not just for hackers and criminals. It provides benefits to regular, law-abiding citizens as well.
So what is the Tor network and how does it work, exactly?
The Tor network allows you to use the internet anonymously without having to worry about your activity being tracked. This is achieved by encrypting your traffic and bouncing it around three nodes on the Tor network before sending your internet request to the website you want to access. This in effect hides the IP address of your device. Without the true IP address of the source device that sent the internet request, websites (and other watchful eyes) will not be able to determine the origin of your request.
This complete guide will take an in-depth look at how Tor works, as well as the benefits (and shortcomings) of using the browser. The information provided will allow you to decide if you want to consider Tor when using the internet.
Let’s get into it.
What does Tor stand for?
Tor stands for The Onion Router. It’s an internet browser just like the one you’re using now.
It allows you to search the internet and access websites just like your Google Chrome or Mozilla Firefox browsers do. But there’s more.
Tor isn’t your ordinary browser.
What is Tor used for?
Anonymous internet browser
When using Tor, your online activity is anonymous.
This means you can’t be tracked by your internet service provider (ISP), Google, or any other third parties that keep a record of your online activity.
This is a problem that many people don’t even realize the extent of. Google and other third-party companies are taking note of every search you perform and website you visit online. They sell this information about you to marketing companies. The marketing companies then serve you targeted ads in an effort to get you to buy the products of their clients, whether you really need them or not.
To put it simply, Tor provides the privacy that many internet users want, but very few have.
Portal to the dark web
As mentioned at the beginning of this article, Tor also provides you with access to the dark web.
What exactly is the dark web?
The dark web consists of all the websites that can only be accessed by Tor. These websites are not indexed by the other popular web browsers like Google Chrome or Mozilla Firefox. This basically means that there are sites on Tor that are “invisible” to the rest of the internet. That’s why it’s called the dark web.
Tor gives you the keys to the dark web, but you must enter at your own risk. We will explain this in further detail later on.
How does Tor work?
Tor allows you to browse the internet anonymously, but how does it do this?
The answer here involves hiding your actual IP address from the rest of the internet.
For those of you not familiar, an IP address is basically an identifier that is assigned to all devices that are connected to the internet. That’s how websites are able to send your browser the websites you want to see. They answer your internet requests by listing your IP address as the destination of their responses.
Normally when you go to a website on your internet browser, your ISP, Google, other third parties, and the websites you visit are all able to see that your internet requests are coming from your IP address. If you mask your true IP address when you submit your internet requests, they won’t be able to determine that the internet activity came from you. Thus, you have achieved internet anonymity.
Easy enough right?
Let’s dive into the components involved with Tor.
Tor nodes
The Tor network is made up of many servers and computers that are used to make requests on behalf of the user (you). These systems are called nodes or relays, and without them Tor wouldn’t be able to function.
In fact, any Tor user can set up their device as a Tor relay if they so desire. The more relays that make up the Tor network, the faster and more efficient the experience will be for those who use it.
Tor node hosting considerations
If you’re thinking about hosting a Tor node, it’s important to know that all nodes in the Tor network are visible in a public directory. In other words, if someone knows your IP address, they’d be able to tell if you’re running a Tor node.
If you’re the host of a Tor relay, the government may be suspicious of you because of the illegal activities that occur using Tor. This may attract unwanted attention from the government if they know you’re an active contributor to Tor. That said, if you’re not doing anything illegal this is nothing to worry about.
Another important consideration is if you run a relay on Tor, you may become a target of hackers. If a Tor node becomes compromised by a hacker, the hacker will be able to see the IP addresses that are using the node. If multiple nodes become compromised by the same hacker, they may be able to piece enough information together to identify a Tor user.
This has happened in the past where criminal users on Tor have been identified (detailed later).
Tor proxies
When a request is made in Tor, it goes through three Tor proxies before reaching the intended website. The purpose of the three proxies is to hide your IP address from the website you’re visiting. The connections between the proxies is also encrypted to prevent others from listening in on your requests.
Each proxy adds another layer of encryption on top of the previous proxy, like layers of an onion (hence the name The Onion Router). When a request is sent to a website, a layer of encryption is peeled off at each proxy until it gets to the site. This ensures that the Tor traffic is all encrypted from the user to the exit node.
The three proxies used in a Tor request are:
Guard node
The guard node (or entry node) is the first proxy that your Tor requests will go to.
When you log into the Tor browser for the first time, a small random set of guard nodes is assigned to your device. These nodes have been identified as extremely secure and unlikely to be compromised. If the guard node isn’t compromised, you can be confident that you won’t be identified when using Tor.
Each time the Tor browser is used, the guard node is assigned from the small set that was randomly assigned to your device.
Middle node
The middle node is the second proxy that your request will go to.
Once a guard node is chosen for a connection (also known as a circuit), the middle node is randomly chosen from the list of public tor nodes.
Exit node
The exit node is the last proxy your request will go through. It communicates directly with the destination website that was entered into the Tor search bar.
Much like the middle node, the exit node is randomly assigned from the list of public Tor nodes.
Node assignment
One item of note is that the exit node for one Tor user could be the middle node for another user. Every user will use different nodes for each of the three proxies. This unpredictability adds another layer of security to the Tor network. The more nodes in the Tor network, the more difficult and confusing it is to determine the real IP address of a Tor user.
Tor process
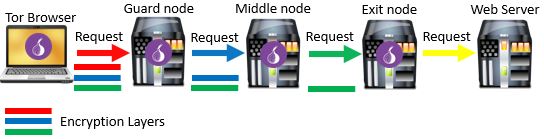
Now that you understand the Tor network and the proxies it uses, let’s go through the process of sending an internet request through Tor.
Request
The process begins when you’ve opened the Tor browser and enter a website you want to navigate to. In this case let’s use the Tor version of Facebook (with a .onion domain).
At this point, the public directory of all Tor nodes is accessed and a node is chosen at random to serve as the first Tor proxy, or the guard node. The connection between the user’s device and guard node includes three layers of encryption to ensure confidentiality of the request. There’s one layer of encryption for each of the three Tor proxies that will be used. Each of the three layers of encryption is peeled off at each Tor proxy in the process.
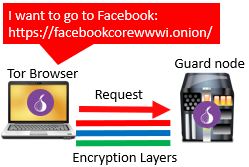
From the guard node, the request is sent to a second proxy. The second proxy is the middle node. Much like the guard node, the middle node is also selected at random from the Tor node directory.
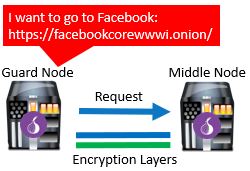
Once the middle node receives the request, a second layer of encryption is removed. At this point only one layer of encryption exists on the traffic. At this time, an encrypted connection to the last proxy is established. This is the exit node.
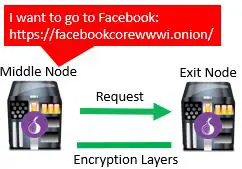
Once again, another layer of encryption is removed, but this time between the middle node and exit node.
From the exit node, the request is sent to the website that the user searched for.
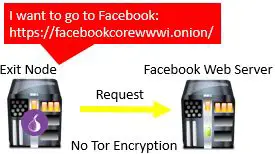
Due to the fact that the requested website is not part of the Tor network, there is no encryption built into the final leg of the process. However, if the website that was entered into the search bar uses https (as most do) or has a .onion domain name, the connection between the exit node and website will be encrypted as well.
The entire request process using Tor looks like this:
Response
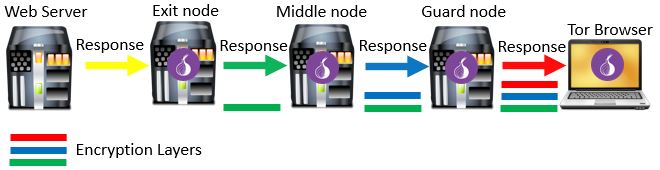
When the website receives a request for its webpage, it treats it like any other internet request. The website will see that the request came from the Tor exit node, as that is the IP address that requested the website. It will reply to the Tor exit node with the webpage that was requested.
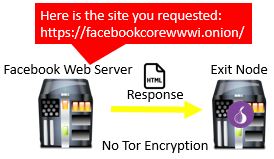
At this point the Tor exit node receives the webpage from the website. In reverse fashion, the exit node adds a layer of encryption to the connection between the exit node and middle node. Over this encrypted connection, it sends the requested webpage to the middle node.
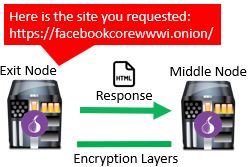
The middle node receives the webpage from the exit node. It follows suit and adds a second layer of encryption between it and the guard node. The requested webpage is then sent to the guard node over the encrypted connection.
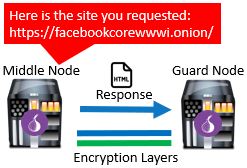
The last leg of the response is between the user’s device and the guard node. The guard node will receive the requested webpage from the middle node and add the final layer of encryption to it. After adding the final layer of encryption, the webpage is sent to the Tor user’s device.
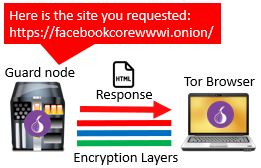
The Tor user’s device receives the requested webpage from the guard node. It then strips the three layers of Tor encryption from the message so the webpage can be viewed in the browser. This completes the process of a request using the Tor browser.
The complete response process looks like this:
Could I still be identified on Tor?
Using Tor to browse the internet anonymously isn’t foolproof.
There have been cases where Tor users have been identified and arrested for illegal activity.
How does something like this happen? Let’s take a closer look.
Compromised Tor nodes
As mentioned earlier, if all three of the Tor nodes that your connection uses are compromised, you can be identified.
Granted, this is extremely difficult because there are many Tor nodes that make up the network.
Tor also takes extra precaution when assigning the guard node. If a node doesn’t meet the strict security requirements established by Tor, it can’t be used as a guard node. On top of this, the middle and exit nodes are selected at random when you start a Tor session.
Despite all these precautions, Tor users have been identified in the past.
There are even suspicions that the federal government hosts nodes on Tor. If you host a Tor node, you can see all the traffic coming into and out of that host. This can provide valuable hints when trying to piece together a Tor user’s identify.
To be clear, if you’re acting lawfully while using Tor you have nothing to worry about. Just know that you may not be as anonymous as you think if you’re doing things you shouldn’t be doing.
Signing into accounts
Just because you’re using Tor doesn’t mean you’re invincible.
This may seem obvious, but logging into your social media or Gmail accounts while using Tor will give away your identity.
If you want to stay anonymous, don’t do this. If you’re going to be logging into one of your personal accounts, you might as well use a regular browser.
Using JavaScript
Another way you can be identified when using Tor is if you have JavaScript enabled. JavaScript can be used to initiate a direct connection to a Tor user, giving away their IP address. Once your IP address is uncovered, you’re no longer anonymous.
So you just need to disable JavaScript in Tor and you’re all set?
Unfortunately there’s a catch here.
Many websites require JavaScript and Flash Player to work properly. If you were to disable these applications, many of the sites you want to go to won’t work as they should.
Once again, if you have nothing to hide you may want to use Tor with JavaScript enabled. Chances are, you’ll only be identified on Tor through JavaScript if the authorities are suspicious of you. On top of that, you’ll have a much better experience using Tor with JavaScript enabled.
Websites that use http
If you access a website that uses http, your activity on Tor could be tracked. This is because the last connection between the exit node and web server is not encrypted unless the website being accessed uses https or is on the .onion domain.
What’s so risky about this?
For one, you don’t know who is controlling that exit node. The host of the exit node can monitor or even alter your traffic if he or she wants to.
For example, if the federal government is hosting the exit node, when you send your internet request through Tor they can send you a website with viruses on it. If you download the virus it may identify your true IP address and expose you.
This may sound far-fetched but it has happened before. You need to be aware of this if you’re going to use Tor.
Tor pros and cons
Now that you have an idea of how Tor functions, let’s spell out the benefits of Tor, as well as its downsides.
What is Tor good for?
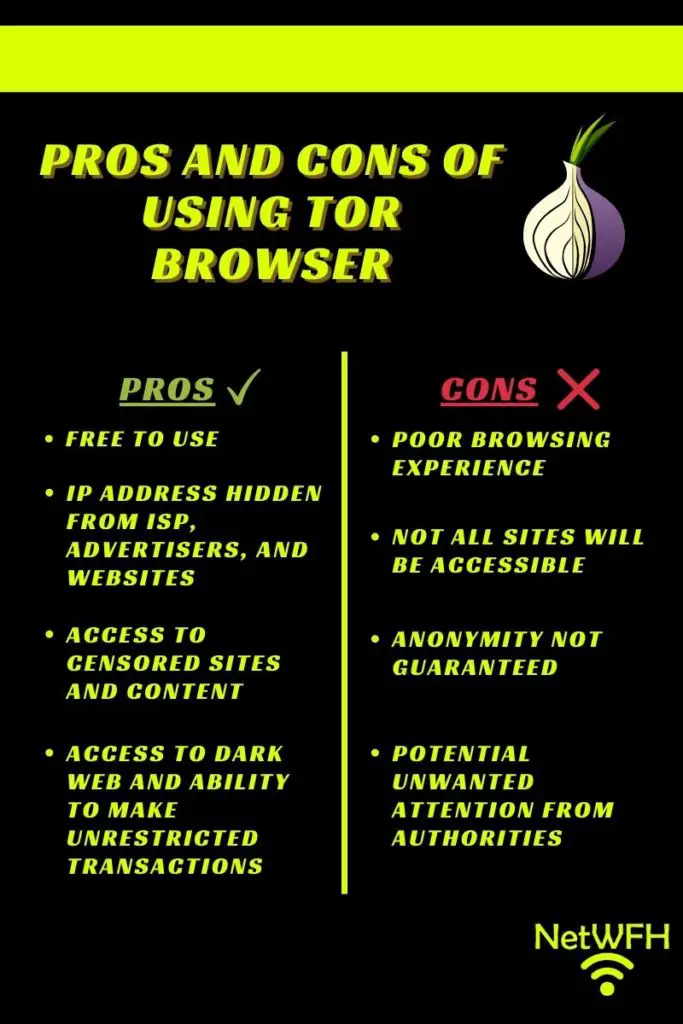
Free to use
One major benefit about Tor is that it’s free to download. If you’re curious about it, you can download it and try it out to see if you like it. Other alternatives (like Virtual Private Networks) cost money, so this could be a nice cost-free alternative for you.
Privacy on the internet
With Tor you can feel good about using the internet privately. If you’re using it correctly and not doing any illegal, you can be comfortable that your activity is most likely anonymous (see downsides section).
Access to censored sites and content
Tor masks your true location by hiding your IP address. This allows you to sidestep any restrictions that your government or organization might put on certain websites and content. In this sense, Tor provides you with more freedom on the internet.
Who can argue with that?
Dark web access
By using Tor, you’ll have access to sites and resources that other browsers don’t provide. On the dark web, you’ll be able to speak freely and make unregulated transactions with other users.
Of course, not all these transactions are legal, so you need to be careful about how you’re using Tor.
Downsides to Tor
Poor browsing experience
Browsing on Tor is much slower than using a regular browser due to the fact that each request bounces to three Tor nodes before reaching its destination. This will take longer than accessing the site directly like on a normal browser. Tor may take some getting used to and may result in some frustration when you’re starting out.
If you want to ensure anonymity when using Tor, you have to make some sacrifices. As mentioned earlier, you’ll have to disable JavaScript, which will negatively impact your experience. Many websites won’t even work without JavaScript. This is something you have to live with if you’re committed to using Tor.
Not all sites accessible
Another factor to consider is that not all websites work with Tor browser. This is something to consider if some of your favorite sites won’t work with it.
Anonymity not guaranteed
Just because Tor advertises that it provides anonymity on the internet doesn’t mean it’s foolproof. As mentioned earlier in this article, there are still ways to identify Tor users. You need to be aware of this if you’re planning to perform illegal activities on Tor.
Potential unwanted attention from authorities
Tor can have a negative reputation because it provides access to the dark web. Many people assume that Tor users access the dark web for illegal purposes as a result. Unfortunately the same is true for law enforcement. It’s impossible to say for certain, but they may pay closer attention to you if you decide to use Tor.
This isn’t meant to scare you away from using it. As mentioned several times in this article, if you aren’t doing anything illegal you have nothing to worry about.
Should I use Tor?
Tor is a great, free way to maintain your privacy on the internet. With that being said, if you decide to use Tor you’ll most likely have to make some sacrifices. It boils down to the question of how much your privacy is worth to you.
If you’re looking to remain anonymous on the internet and are willing to pay a few dollars for it, a Virtual Private Network (VPN) might be a better option for you.
VPNs are faster than Tor, and you can access all the websites that your normal browser can access. You can’t access the dark web with a VPN, but all normal internet functionality will be available to you.
You can also use Tor while connected to a VPN if you still wanted to access the dark web and remain anonymous.
VPNs hide your IP address, but they do it a little differently than Tor does. Many people are willing to pay a few dollars for anonymity and full access to the regular internet.
To learn more about VPNs and how they work, check out our previous post: Will a VPN Hide My Location or Can I be Tracked?
Where to download Tor
If you want to try Tor, you can download it from the Tor Project website. Make sure you download Tor only from this site, as other sites might include malicious software with the download.
Wrap up
Now you should have a good idea of what the Tor network is and how it works.
If you would like to learn more about other products and services that provide privacy when using the internet, check out the following posts:
What is Incognito Mode Used for?
Will a VPN Hide My Location or Can I be Tracked?
If you have any questions, feel free to comment below or reach out to me on the Contact Me page.
